IKON Announces ISP SNIFF Service

The team at IKON is pleased to announce our ISP SNIFF Service. IKON’s ISP SNIFF Service allows us to search for Internet Service Providers in your areas and request a bid for services based on your school’s specific needs and selection criteria. We offer this service free of charge to K-12 schools. In addition, we […]
Devices Hacked by Linux Malware
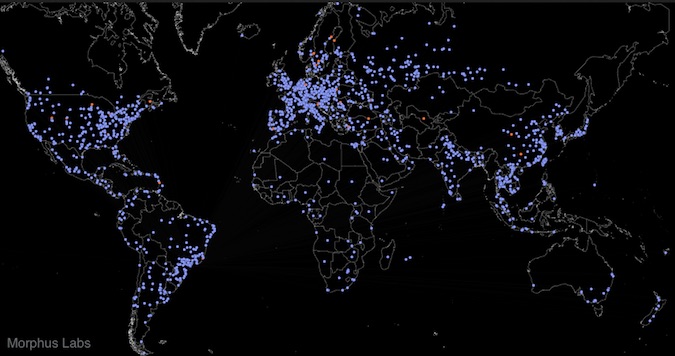
Thousands of devices have been hacked by a Linux malware named Rakos, and while researchers have yet to see any actual malicious activity involving the botnet, they believe it could be used for powerful distributed denial-of-service (DDoS) attacks. Rakos, whose existence was brought to light in December 2016 by ESET, targets Linux systems by launching […]
